Supreme Internet and Email Security Threat…What You Need to Know and Do NOW
Have you heard about Astaroth? Until 2 days ago, I never had. I wish I didn’t. You will too. However, it’s critically important to understand the implications if you’re a Google, Gmail, Microsoft Outlook, Yahoo, AOL or basically an internet user at all. Astaroth is a highly sophisticated ai-aided hacking tool. I won’t go into the technical details, not sure if I fully understand to be honest. The down low is that websites and urls are duplicated, well enough to fool users into logging in or clicking links under a variety of pretenses such as to enhance your security. Then the hackers even have the ability to override 2-step authentication steps (and we thought those kept our info secure). How? Apparently the codes are intercepted in real time. Consequently, if your data isn’t used immediately, it’s ripe for sale on the dark web. Passwords, user names, profile information, you name it, they’ve got it.
From what I gather, once you’re hacked, a reverse proxy, which is a server that plants itself in front of legitimate servers then monitors all the communications between you and your legitimate browsers and websites.
Then there’s those annoying cookies. They’re also intercepted which may sound like yay, someone else has to deal with them. Except that those captured legitimate cookies containing your info are inserted into the phony browsers.
Unfortunately, the victims have no alerts that a compromise has occurred. All appears normal.
Bottom line from security experts and the FBI.
The latest nefarious scam can threaten your internet and personal account security. Take measures now.
Image modified. Original by Pete Linforth from Pixabay
Rather than me providing links for you to follow-up on this topic, which may or may not be compromised, I encourage you to embark on a safe search to learn more right away.
Truly, with all the global upheaval going on and the degree to which we need to keep up our guard, it’s inevitable that one day when we’re tired, brain-fogged, distracted that things will get passed us. All we can do is try our best to keep ourselves, our information, our property secure. I wish us luck.
Before you unsubscribe from any email solicitations or engage unsubscribe services, read these advisories. Image adapted from original by Denis Bogdan from Pixabay
I use the block feature to permanently delete these type of spams without a reproducable business address
Is it a pipe dream to maintain an organized email inbox when junk mail is relentless? I don’t know, but I sure try.
I use Microsoft Outlook as my email manager. Outlook enables me to house both my professional and personal email boxes within different folders in one convenient location. Nearly every day, I add more rules to identify and permanently delete pernicious spam. I use the ‘block’ feature for one-off spams or those which appear to come from a person rather than a commercial address. Think sex solicitations—yes I now get those daily. If those supposed women only knew who’s at the other end. These are particularly annoying as they’re more difficult to define an applicable rule to associate with a name or address. Most don’t contain my commonly blocked obscenity words, so these slip through. Unfortunately, every year they seem to arrive with greater frequency. Why isn’t my service provider catching this obvious junk? Good question.
If you’re also fed up with spam, have you considered unsubscribe services that will monitor incoming emails to save you the hassle? Before you sign up, I heartily advise you to read this article from Wirecutter, “Email Unsubscribe Services Don’t Really Work. Follow This (Free) Advice Instead”. Their research on each of the unsubscribe subscription vendors via a variety of parameters is useful in order to guide decisions before you sign up.
There were 2 critical points missing from the article that I must emphasize.
1. Before unsubscribing from any solicitation, verify the sender’s email address. While spoofing is becoming more common, it’s at least a place to start. Does the email appear to come from an individual or a verifiable business domain? Are there obvious spelling or syntax errors? Ascii characters (*&@^&*) are often a clue that the email is spam.
2. Never unsubscribe to any solicitation unless you’ve previously had a relationship with the vendor. For example, you’re probably ok unsubscribing from an author whose freebie you’ve downloaded or a department store where you transacted either in person or online. By law, more specifically Controlling the Assault of Non-Solicited Pornography and Marketing Act (CAN-SPAM Act) companies are required to provide an easy opt-out option and honor that request. At the bottom of each of my newsletters, there is an unsubscribe option. If my newsletters aren’t serving you in some way, go ahead and safely opt out.
Emails arrive from this supposed vendor just about every day, that doesn’t mean I can trust them. I’ve never transacted with them previously. Are they legit? No idea, so I won’t click any links. Sometimes my rules auto-catch and delete. Other times, I have to manually trigger the permanently delete rule.
Currently, there doesn’t appear to be a sure-fire, end-all spam messages mechanism. Using rules, filters, and safe unsubscribing practices will at least cut down on the spam enabling somewhat easier maintenance of your email boxes.
Password Insecurity
As someone who has been notified more times than I can count that investment accounts have been breached, had credit card numbers fraudulently used, and checks written against our bank account with an outrageously obvious illegitimate check, I have multiple reasons for embodying transactional trust issues. Therefore, I don’t store a password file on the cloud. Granted by simply logging into websites, my user names and passwords are subject to felonious interception. There’s not too much I can do about that at this point. I could resort to only in-person transactions rather than on-line; however, that may not be a resolution since my credit card was duplicated after using it in-person.
Tracking countless and complicated usernames and passwords is a complex task. For those with memory issues or the inability to keep track of information, that becomes overly onerous. So I don’t fault anyone who has resorted to online password managers. It particularly makes sense for caregivers and money managers who are managing day-to-day transactions and bookkeeping. Easy access for family members who need to be ready to jump into action should a tragic circumstance happen to another family member justifies some system of sharing.
Read about two major data breaches at LastPass password manager. Decide what password storage options are right for your security concerns. Image by Gerd Altmann from Pixabay
However, like with just about everything in life, password managers and cloud storage comes with risks. If you are a user of LastPass or considering investing in LastPass or a similar password management program, I advise you to read this LastPass.com security bulletin. Rather than me getting all techy and attempt to translate what happened, please read for yourself the details about two recent breach incidents and measures LastPass is taking in response. Then decide for yourself what makes sense for the best course of action. Changing all user names and passwords is likely a first step to ensure your logins are more secure.
Easy Way to Permanently Zap Emails in Outlook
If you don’t use Microsoft Outlook as your email manager, you can stop reading now. This tip will only apply to a select few, but if you’re one of them, it may be the win you’re looking for. Before I begin, a couple of things:
1. I consider myself fairly tech savvy. The person many of my friends and some family members come to in order to solve their tech woes. That being said, it took me freaking forever to discover this long-sought after tip. Once you read it, you’ll probably be thinking seriously chick? That’s so elementary, everyone knows that.
2. As you might imagine, being an organizer, I crave empty email boxes. Like that’s ever sustainable. They fill faster than I can empty them. But it sure feels good momentarily.
3. This tip will save you an extra step and keep two of your email boxes fairly cleared out (until the next batch arrives).
What’s the Outlook secret (obviously it was a secret to me)? When you delete an unwanted email where does it end up? In the trash folder. That means, inevitably if you don’t want trash emails eating up storage space, you have to occasionally dump the trash. How do you avoid trash build up? Turns out it’s easy if you know what do to, which I didn’t until earlier this year. How did it take me so long to figure this out???
After reading the email, if you wish to permanently delete it (i.e., not clog your trash can), simultaneously press the ‘shift’ and ‘delete’ keys. Next, select the ‘Yes’ button when the program asks if you wish to continue. That’s it. Gone.
Want to nix multiple emails? Click on one email, then using the ‘shift’ and up or down ‘arrow’ key select as many emails as you want. Next, simultaneously press ‘shift’ and ‘delete’ keys. Boom, massive permanent deletion without trash can congestion. When mass deleting, slow down enough to ensure there’s nothing you’ll need to refer back to in the future like an important note from your boss or invitation details.
Maintain control over e-mailboxes in a snap. The secret is out.
Recharging my emotional state with much needed email-less relaxation while my inbox manages itself
Summer travel has wound down, so this tip may feel like an after-the-fact suggestion. However, some folks in my circles have already begun planning their winter holiday trips, and even scheduling summer 2023 vacations. We have a lot of lost time to make up for.
A few days ago, I returned from extended travel during which I intentionally avoided opening my email as an emotional rescue remedy.
Upon my return home, I was super grateful that I had pre-organized my mailboxes (personal and professional) to minimize inbox overwhelm. The prep had only taken minutes using Outlook, my email managing software. Fortunately, most of the emails that remained in my inbox when I finally got to it, were those that needed my attention on some level.
Your email program operations may differ, but the general ideas will be the same. I’ve broken the process down into 3 simple steps to “know before you go”.
1. ‘Rule’ Out Junk Mail
For both my professional and personal inboxes, I’m finicky about who gains access. I continuously monitor for junk mail and block senders or set up electronic rules to permanently delete spam. Spam still gets through via devious practices which is why not all rules work. Therefore, unfortunately this process isn’t a once and done. However, ruling-out spam from the get-go will significantly cut down on unwanted emails.
What do my rules look like? Using Outlook Rules Wizard, select the condition specifying certain senders or to search for words/phrases in the body, message header, or sender’s address. I recommend separate rules for the body, the header, and sender’s address in case your program requires that those words appear in all the locations before it activates. The rule may not apply if the word appears in one OR the other.
Click on the checkbox for “specific words” in each location and add every pornographic, salesy, or undesired vocabulary you can think of. Keep in mind, if your bestie sends you off-color emails, that may get deleted based upon your rules.
Create rules to search for specific undesirable words in various locations within received emails.
Choose an action to process your rule. In this case, I selected permanent deletion.
2. Notice and use categories
After reducing junk mail, watch for categories. Do you receive emails from home décor shops? Office supply vendors? Self-improvement practitioners? Professional Associations? These are just a few to help get your brain and eyes detecting patterns. Had I not set up category filters and corresponding folders before I left, I would have had hundreds of emails in my inboxes when I got home. How did I do this? I watched my inbox for a few days. Then I created about ½ dozen subfolders in my inbox based upon the categories I listed above which reflected the non-critical emails that flowed in. In Gmail, set up labels in lieu of folders.
Then I started defining rules in Outlook. Other programs may classify these demarcations as filters or labels. Next, I selected each email, and created a condition such as look for a specific sender. You only have to do this once per sender. Therefore, if you have multiple emails in your inbox from the same sender, no need to repeat this step for each email.
The next step was defining an action to take. In this case, I set up the rules to move those senders’ messages to specified folders. For example, each time it detected an email from NAPO, my professional association, Outlook sent it to the NAPO folder. Considering every day, I receive a daily digest from NAPO along with emails from my local NAPO chapter and special interest groups within the organization, that would have resulted in a massive amount of weight in my Practical Sort inbox. Instead, they were neatly tucked into the NAPO folder for me to review when I have time.
3. Delete excess immediately to fully focus on critical emails
For your postal mail, it’s advisable to have your recycling bin nearby to immediately toss unneeded and unwanted flyers, solicitations, envelopes, etc. to prevent clogging your countertops and desk surface. Same goes for email. Prevent e-waste and running out of data storage by eliminating useless e-refuse. Make use of your email trash bin. In fact, if you’re brave enough, permanently delete the waste. If that feels too extreme, leave behind any emails in the trash until you’re fairly certain you won’t need it such as a conference registration that happened last year. Rather useless now.
Drag emails needing further action down to the Task icon. Create due dates and times to stay on schedule.
Once you’re ready to sit down with your email, go through your inbox to see what needs your attention right away. You can highlight these with a flag in Outlook or a star in Gmail. For those needing action, I dragged them down to the Task icon. Each task was assigned a start and due date/time reminder to avoid falling through the cracks. Gmail also offers task setting with corresponding due dates.
When you have time, browse through the subfolders you created. Some of my subfolders held nothing of interest, so I did a mass permanent deletion by highlighting all the emails, then hitting ‘shift and delete’ simultaneously. My spam folder was packed with junk, for that I tapped ‘empty folder’ which is set to permanently delete all messages. I don’t want any unwanted emails to go to my trash bin because that results in an extra deletion step. Touch it once, and be done.
Working my way through my inbox literally took minutes. Had I not prepared prior to leaving, scouring through the gold vs detritus would have taken an hour or more when I’m already backlogged and needing all the time I can get. Granted there are tasks to do as a result of the emails which I haven’t gotten to yet. However, I can now approach those in a more guided and thoughtful way.
Keep in mind, as a courtesy, you can set up email “out of office notifications” to let senders know that there will be a delayed response. When choosing dates, give yourself a few extra days after your actual return to buy yourself time to reacclimate and get back up to speed to avoid unnecessary overwhelm.
For more guidance on managing email, check out these additional Practical Sort tips. 5-Minute Email Purgefest; Declutter Thy Neighbor: Email Courtesy; Stop, Don't Open That
We all know that we need to keep our eyes peeled and ears perked for signs of danger. There are days where I feel bombarded by perils due to pandemic risks, cars whipping through stop signs in my neighborhood, and the onslaught of tech viruses and malware. What’s more concerning is learning that the some dangers were detected months before alerts are sounded. This has happened countless times when our personal data has been hacked or potentially hacked. After a while, sincerity by companies stating, “We regret to inform you that despite taking extraordinary measures your personal information may have been compromised. However, we are tightening our security procedures to prevent further intrusion…” Yada yada. If they sincerely regret their security weaknesses, they might have thought about informing us earlier so that we can take protective measures immediately. Granted in some cases software fixes need to be created so that updates can be downloaded.
Have you heard about the latest Apple security flaw? And the update patch to block the leaky intrusion door? I heard about it on a news screen ticker, then saw additional information on a daily digest thread among NAPO Organizers which reminded me to take action.
If your gadgets aren’t set to automatically update or you didn’t receive an update alert on your Apple Iphone, Ipad or Ipod, here’s what you need to know. Mind you, most of the information I learned about the flaw was via news reports, not Apple’s support website. My phone also did not alert me to the update. Additionally, I’m on the third attempt to execute the update due to error messages. Sigh.
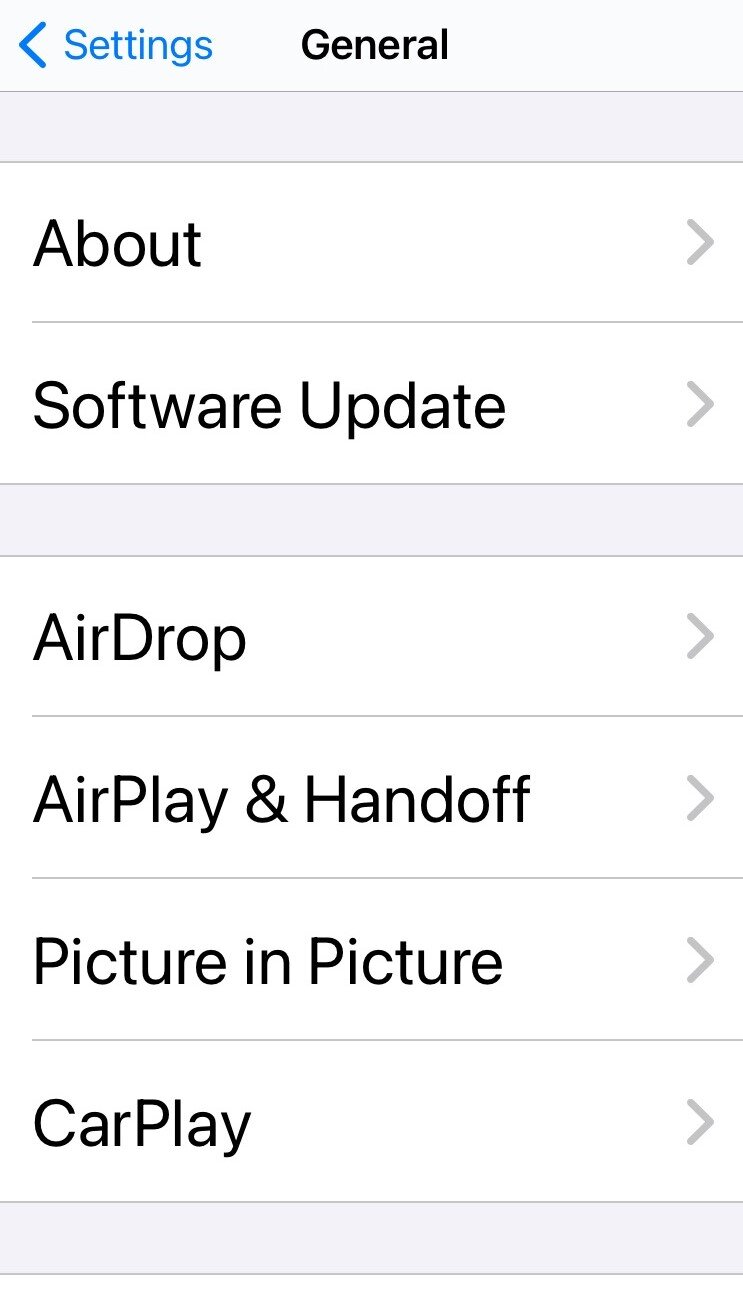
1. You’ll need to download iOS or iPadOS version 14.8. The following directions are for iPhones. You may need to do some digging beyond that.
2. Go to Settings. Tap General. Tap Software Update. At the bottom of the screen there should be a button to download.
3. It’s recommended that you back up your device prior to updating.
4. Plug your device into an electric outlet to recharge if the power is low before updating.
For more information on the invasive spyware threat and suggestions for determining if you’ve been infected, here’s an article from CNET.com, “Apple's iOS 14.8 Pegasus security fix: iPhone owners urged to update immediately”. This article explains about the “Pegasus” spyware risks and potential remedies. They also recommend a software app that can detect if your device shows signs of infection. Full disclosure I have not tried that app, and I’m not sure I will at this point.
By the way, according to various news reports, the threat was first detected in February. If true, that was 7 months ago. Yep, I’m feeling secure.
5-Minute Email Purgefest
Paper and email, the 2 fastest clutter bugs at home and in the office. They also happen to be 2 of the most requested types of appointments I receive. In my case, that works out well for me because during the pandemic, I’m only offering virtual assistance. Paper and email are more amenable and easily tackled virtually than rearranging cupboards and furniture.
Here’s a suggestion to whittle down the email folders. HOWEVER, and it’s a giant HOWEVER, you have to remain committed to the process because the flow doesn’t stop just because we want it to or after one stab at it.
In my March 2020 blog, I discussed setting up filters and rules to minimize junk mail inflow. Unfortunately, although these tools slow the torrent, they doesn’t eliminate the flow. Spammers are getting more diabolical. Slight adjustments to sender names and addresses by adding a dash or an ampersand or other ‘clever’ disguises, and your back to square 1. It’s appalling and a nuisance, but for now, here’s another option aside from the rules and filters.
No surprise that I have little tolerance for physical or digital clutter. Therefore, I like to keep my email boxes as minimal as possible using 5 minute purgefest breaks. If I have a few minutes prior to an appointment or before I wish to start a new project, I set a timer for 5 minutes. I sort my emails by sender then begin purging. There are certain senders that I know I can wipe out lock, stock, and barrel without taking time to reread their messages especially if I’m working on emptying the trash bin.
Here’s how the 5-minute Purgefest works in Outlook 16 which is the email program I use. You can check your email provider’s specifics for mass email deletion.
Set a timer for 5 minutes when you have a window in your calendar. My advice is to look for windows in lieu of social media cruising or other distractions unless it is a physical outlet break for sustenance, movement, breathing.
Select a folder you wish to tackle.
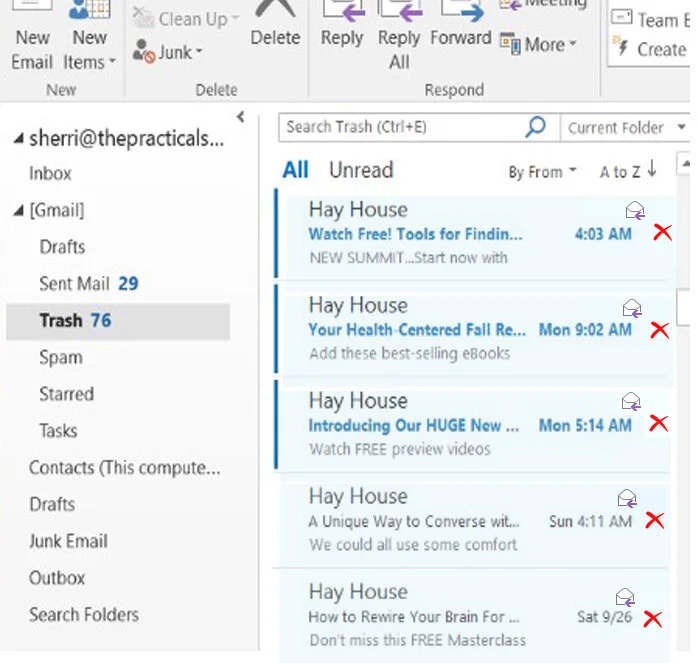
SORT
Sort by sender, date, subject, or whichever filter suits your needs. I sort by sender. In the example in the photo, I started with the first message in the list from Hay House. Then the purgefest began.
PULL-DOWN MENU DELETE OPTION
Either right click for a pull down menu and hit ‘delete’.
HIGHLIGHT
Hold your shift bar down as you scroll to the last consecutive message that you wish to ditch.
Still holding down the shift bar, select the bottom message. Now all the ‘to-go’ messages are highlighted.
If you realize you missed more consecutive messages, keep holding the shift down and go to the last message you can see that is a goner. Then reselect.
CLICK 'X' DELETE OPTION
Or click any ‘X’ that will appear next to the envelopes and dates to the far right of any of the highlighted messages.
In this case, in less than 5 minutes, my trash can downsized from 76 messages to 2. I left it at 2 because there are 2 messages that I want to review before permanently deleting. Cringingly, by the end of the day, my trash can will likely be nearing 70+ again. This is an ongoing exercise, but easier to stay on top of than digging your way out the MASSIVE weight.
This looks and feels so clear. It didn’t start out this way.
Messy Cable & Cord Solutions
Do you hate all the messy cords and cables around your desk? Every so often I address this issue in my own office. Most of my efforts have been the cables that hang behind my desk. Those I’ve mostly secured to my rear desk legs with Velcro which has eliminated some of the tangles and unsightliness, not all by any means. Those trailing along my desk surface have been irritatingly gnawing at my aesthetics and need for organization.
Here’s what I’m dealing with on the surface.
1. Power cord for the laptop.
2. Monitor cable for my external monitor.
3. Printer cable (our wireless is down too often)
4. Mouse cable
5. Speaker cable
6. Keyboard cable
7. Internet cable (again our wireless is wonky)
I chose for my 4 port Hub, 2 on each side
That’s a lot. I could use wireless peripherals, and perhaps when the hardware dies, I might go that route.
As you may have noticed, newer laptops are equipped with fewer USB ports. Here’s my latest trick. A USB port hub. You can find them with 2-7 ports on a hub. There may even be more slots available, 7 was the max I’ve seen, and they’re relatively reasonably priced. There are options for layout too. You can get all the ports on one side of the box or as I chose for my 4 port hub, 2 on each side so I have more flexibility for where it resides and from which sides the cables are inserted. I also bought another hub for another laptop with all ports on one side.
Unfortunately, my external monitor cable needs an alternate connection port not available on the Hub
Unfortunately, my external monitor cable needs an alternate connection port not available on the Hub, so I still have that cable feeding into my laptop, but now I’m down to 3-4 (power cable, external monitor, USB Hub and possibly speakers) if I decide to keep my speakers for use with this laptop. They’re usually used on another laptop.
This leaves extra ports for external backup hard drives or if I need to reinstall software from a cd (that happened 2 days ago), I can easily connect my portable cd drive.
I love how much cleaner my desk surface looks and feels, and the USB mostly tucks behind the laptop. The cord is rather short on the hub so your option for complete invisibility is limited. I understand the short cords on the travel hubs, but I have no idea why the stationary ones are approximately 2“ long. I purchased the black hub instead of a white one and it blends in fairly well with my desk and astride the black printer.
I love how much cleaner my desk surface looks and feels, and the USB mostly tucks behind the laptop.
Finally, label, label, label. You don’t need anything fancy, but with so many look alike cables, you’ll be able to make quicker identifications if you label your cords. You can use adhesive labels or if you don’t have any handy, and if you like a typed look, use paper, your printer and your favorite font. For extra adhesion, I wrapped my adhesive labels in translucent tape.
Screen Sharing Savior
Are you frequently called upon to provide tech support? Perhaps for a senior family member? Just about every few weeks, my mom presents me with another computer dilemma to resolve. She’s 2k+ miles away, and I’m no tech wizard. Now with the pandemic, Zoom family calls, etc., getting mom up to speed has been challenging sifting our way through causes and solutions blindly via the phone.
Then voila, I had a lightbulb moment. Well more likely having first to discover electricity, then inventing the lightbulb, learning how to insert the bulb into a lamp, then determining how to turn it on. Let’s just say it was a process. It took several days with many hurdles to conquer to finally get Zoom working for her. Her desktop computer didn’t come equipped with a camera or microphone which adds a level of complexity. Now with Zoom finally installed, she can share her screen with me so that I can see the hiccups and guide her through step by step to resolve basic issues. Viruses and malware are beyond my pay grade.
If you’re trying to help someone remotely with computer issues, then screen sharing may make your life easier. I don’t have software that allows me full access to her computer and in fact, on several occasions I have advised her not to permit strangers to remotely access her computer. Sigh. I have trust issues for good reason.
If you’re new to all this, I’ll try to take you step by step, but then again there’s always Googling and Youtube if you need further instructions.
Here are a few thoughts before screen sharing.
Setting up a new Zoom meeting
Turn off any programs or documents that are private or you don’t wish others to see.
If you haven’t already installed Zoom (there are other programs available, but I will focus on Zoom as that’s what I use), download the program at Zoom.us and follow their instructions
Depending upon where you store your downloaded files, you will need to retrieve the Zoom launcher there. Most times new downloads will default to your Downloads file.
Click on the downloaded Zoom file and launch.
From there, you can create a free account and set up your profile with a variety of settings including requiring passwords to avoid Zoom bombing (unwanted intruders), establishing a waiting room so that guests have a place to virtually wait until you are ready to greet them, and stylizing backgrounds among many other options. That is all beyond the scope of this tip.
Once you both have Zoom set up, invite your guest to a virtual meeting by scheduling a convenient date or time, send them an email with the details (Zoom will automatically generate an email template for you), or you can just start a meeting and pass along the log in details on the spot. Don’t be surprised, particularly if you’re working with someone who is intimidated by tech, if all this exacerbates tensions and stressors. But you will get through this. We did.
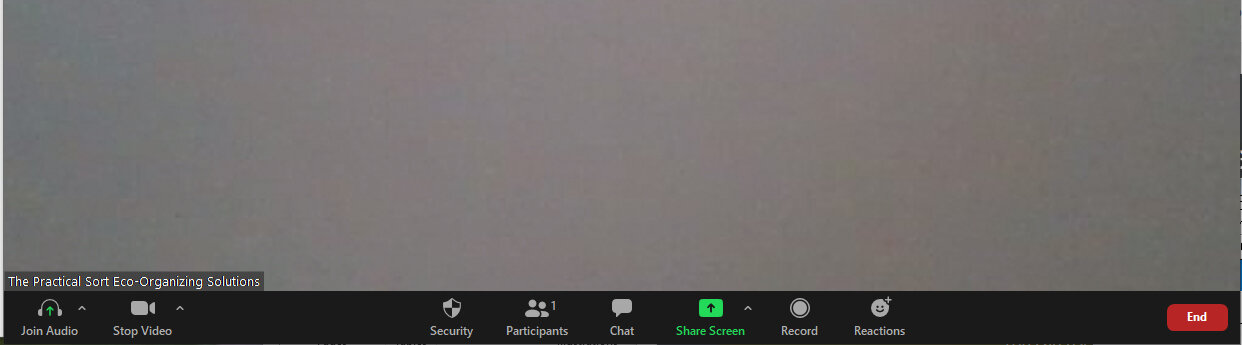
Zoom option buttons
Have your guest select the share button on the bottom of the screen. If they don’t see it, once you run your mouse along the bottom of the screen, options will appear such as Mute, Join with Audio, Join with Video, Screen Share, Record, Reactions, Security, and End meeting.
The Screen Share menu provides you with many options to tailor your conversation
Choose which screen you wish to share
Under the Basic Screen Share Tab menu, the person who wishes to share their screen will be given additional options for which screen they would like to share if they have multiple screens or specific file.
Under the Advanced Screen Share Tab, they can select “Portion of Screen”, “Music or Computer Sound Only”, or “Content of 2nd Camera.”
Under the Files Tab, they may choose to select specific applications or files they wish to share through Microsoft One Drive, Google Drive, or Box.
Back to basic screen sharing.
In my case, since my mom doesn’t have a microphone on her desktop computer, we converse via the phone while I view the glitches and instruct her how to resolve them. Having audio and video capabilities would definitely simplify the process.
Rather than helping blindly, screen sharing enables tech problems to be resolved much quicker especially with populations who might be intimidated by all things tech.
Yikes, running low
Storage Space Recovery in a Few Clicks
How much available storage remains on your cell phone?
My little old iphone was in the red zone. There was little space left for the daily nature photos I grab during walks or any job site photos (if and when I can return to on-site visits), texts I wish to save, etc.
Every few weeks, I download all the photos from my phone to my computer and then another back up to an external hard drive for safekeeping in case my old phone bites it. Next I scouted around for Apps I no longer wish to keep. I recently found some that I never use. 2 are scanning Apps and there were some odds and ends like hotels and list-making Apps.
Nearly doubled my free space, that feels so much better
Presto, they’re gone, and I nearly doubled my available memory in a few swift clicks.
My screen is cleaner now so I can find what I’m searching for faster.
Image by FelixMittermeier from Pixabay
Categorize your photos into folders, then subcategorize into subfolders
If you’re itching for something to do, how about tackling your digital photos? Trash unflattering photos, shots of your exes with painful memories, or any that give a jolt of negative emotions. You’ll free up memory space, searches will go faster, and your mind and hardware won’t be bogged down with mental garbage.
For my blogs and weekly tips, I have accumulated zillions of photos. While most are in files then subcategorized, many are in very broad categories such as food and kitchen. During some downtime this morning, I subcategorized them into subfolders such as recipes and meal planning, drawer organizing, entrees, vegetables, desserts, well you get the picture (pun definitely intended as humor is a much needed elixir).
Sort away. You’re likely to run into some photos that could fit in multiple categories or none at all. No worries, you can always run a search on your computer to find it. Searches seem to go faster from a specific folder such as the Kitchen and Food folder when I’m looking for that type of photo than running a search of the entire computer.
If you find any photos that are breathtaking or evoke dreamy memories, then why not print it out and frame it? You’ll enjoy it much more often then if its buried on the hard drive or cloud somewhere.
Reach out if you have any questions at sherri@thepracticalsort.com.
Image by Gerd Altmann from Pixabay
You’re so happy for your gal pal. She announced that she finally received that long deserved promotion. She sends out a message to all of her friends, family members, coworkers, acquaintances, fitness club pals. You get the picture, this bit of sweet news is going out to just about everyone she has ever met. You’re so happy for her. Yay. Then the onslaught hits your inbox. Your glee segues into exasperation as the congrats and “way to gos” pour in like a leaking deluge from an old water main. There seems to be no let up. Each new arrival eats away at your bytes, time, and patience.
Here’s how you can help. When responding to a group message, try to be mindful about whether or not the rest of the group members will benefit from your reply. If it’s work related, and the team needs to know the details, that’s groovy. If it’s a congratulations, thanks, great job, etc., replying to the sender instead of the group is the courteous decluttering route. Your absence will truly be felt and appreciated.
Handing over access to your computer could be like handing over the keys to your safety deposit box. Risky. Image by Bruno Glätsch from Pixabay
Technology issues, sometimes they're the bane of our existence. Deadlines are looming or bills need to be paid and just as you press send, the screen blanks or wheels spin endlessly as the computer tries to access sites. Nothing happens. You reach out to tech support. They ask you to turn over control of your computer for remote access. It'll be so much easier.
NO! I would never allow strangers access to my computer. Period. Definitely not remotely. I have chosen to spend hours on the phone with tech supports in the past to walk step by step through the problem and potential resolutions. Eventually, knock on wood, we have been able to resolve the issues.
When you give remote access, even if you are watching their cursor, potentially they could be accessing or downloading files or uploading viruses to your system. Be aware of outright scams, but sometimes even those we seemingly trust, might not have our best interests at heart.
Leo Notenboom of Ask Leo! discusses the inherent risks of screen sharing in this tech article “Is it Safe to allow Remote Access to My Machine?” which I strongly suggest reading. A few hours with tech support with you at the reins is advisable rather than handing over controls. Better safe than sorry. And as Leo advises, if possible, make a full system backup prior to taking any other action.
Image by mhoppsy from Pixabay
I am so grateful when others share useful tips with me or on social media not only for my personal use, but to pass along to my family, friends, and followers. Anything to make our lives easier and avoid headaches is groovy. This came across my radar a few days ago, and for frequent travelers and tech users, this is a must-know. To some people like my son, this tip may seem like a “duh”, but to us less tech savvy dinosaurs, it may be more like an “aha”.
You are at the airport or perhaps even an internet cafe when your phone or computer runs out of juice. You’re in luck because there are USB ports available to plug in. Problem solved. But before you do, Suzanne Rowan Kelleher advises in a recent Forbes E-zine article, “Why You Should Never Use Airport USB Charging Stations” to think twice before plugging into a public USB charging station especially at airports. Hackers are targeting transportation and travelers. She quotes Caleb Barlow, Vice President of X-Force Threat Intelligence at IBM Security, ““Plugging into a public USB port is kind of like finding a toothbrush on the side of the road and deciding to stick it in your mouth. You have no idea where that thing has been.” Yuck, that is not only gross, it can be ruinous.
Instead use a regular outlet charger or there are tech options available to block data from entering your device cord. Virus averted, headache avoided.
I am so not a tech geek, but when this warning came across my computer screen I knew I needed to share it with you. My husband, who is a techie, has mentioned a few times over the last several months that he has grave concerns with wide-scale cyber security issues and gaping holes that need plugging on the internet. Last week, the FBI issued a rare public service advisory to businesses and homeowners to reboot routers due to a worldwide cyber hack 1. The encrypted malware can render your routers inoperable or collect information.
Last week as a follow-up to the initial FBI warning, Popular Mechanics Tech Policy writer Eric Limer advises taking measures one step further by "resetting your router to factory settings" 2. He suggests that you have at the ready instructions to get yourself easily connected after the reboot. Once you are back up and running, change your password and download any updates for your firmware.
Ben Herzberg, Threat Director at the security firm Imperva recommends "that anyone with a router that's at least 15 years old replace it with a newer device and that they regularly check for updates to guard against potential new attacks. And while regularly rebooting your router isn't always a necessary part of good security hygiene, he thinks it's good advice to follow this time — considering the source" 3 .
[1][popularmechanics.com/technology/security/a20918611/vpnfilter-malware-reboot-router]
[2][popularmechanics.com/technology/security/a20966735/router-factory-reset-vpnfilter-malware-fbi/]
[3][washingtonpost.com/news/the-switch/wp/2018/05/30/the-fbi-would-like-you-to-reboot-your-wifi-router/?noredirect=on&utm_term=.27d8c3653e8f]
Back UP! A Cautionary Tale
My Microsoft Outlook 16 email program crashed nearly every day last week. Was it a virus? I am not sure. Thursday, it crashed three times while I was composing an email. During the last meltdown, my contacts disappeared. Searching frantically through the ost. and .pst files was fruitless. Customer Support said they were likely gone for good. Gee thanks. That's what happens when they are housed in a temporary .ost file on the server. Why is the default a temp file for something as important as Contacts? Good question.
I ended up recreating my contact file. This time it was a severely streamlined version in honor of spring cleaning only keeping those with current relevancy. But…when I returned to my computer Friday morning, the slate was wiped clean yet again. I had an old .csv file (a comma separated values file which allows data to be saved in a table structured format) housing most of my old contacts and very few of those added over the last 6+ months which I could have resorted to. Instead I chose to try one more time with a truncated list (I am sure I am missing lots of folks).
Immediately upon finishing, I ran an export of the file to an external backup drive as a .pst file (a Personal Storage Table) and .csv for extra precautions. When checking the .csv I noticed groups were absent, so I had to go back and create the groups separately.
About once a week I back up The Practical Sort files to an external source, but the contacts were out of date. I have now added to my calendar a once a month reminder to do a full hard drive back up including all solo and group contacts.
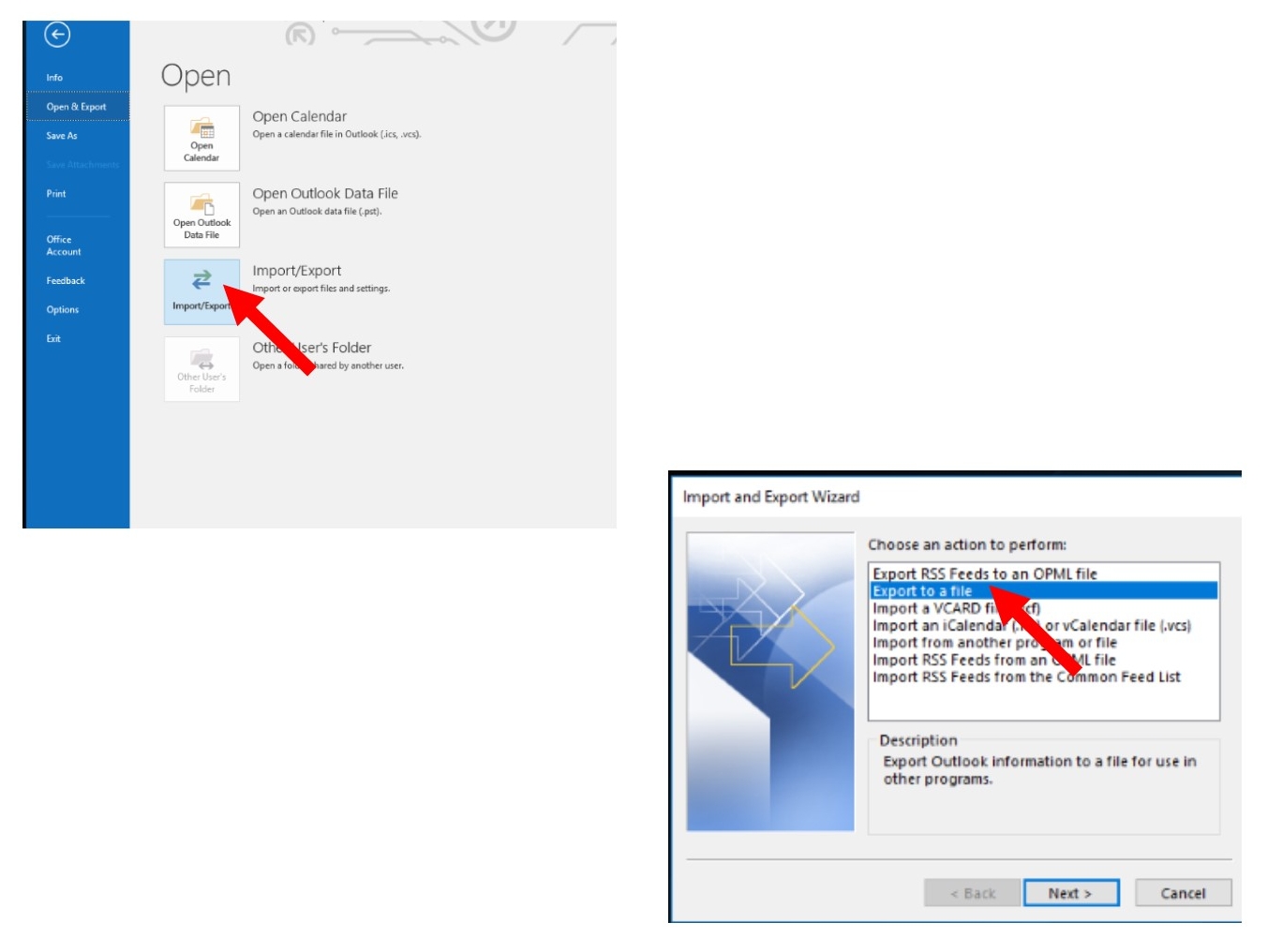
Open Outlook then select File, then Open & Export
If you are using Outlook 16 or any email program for that matter (I cannot help you with the other email client programs), I strongly advise you to back up your emails and all contacts in the event you run into this random crashing problem or any other threat to your mail program.
Back up Contact List
To save contacts as a Comma Separated Values File (csv)
On an external drive (or in the Cloud), create a folder to save your emails and contacts.
Open Outlook>File>Open&Export>Import/Export>Export to a file> Next>Comma Separated Values (.csv)>Export to a File (Select folder to export from: Contacts Folder--scroll until you find your Contacts)> Browse until you find the file folder to store the contacts on the external drive>Finish
Import/Export>Export to a file>
Export to a File (Select Comma Separated Values or Outlook Data File)> Export to a File (Select folder to export from: Contacts Folder--scroll until you find your contacts)> Browse until you find the file folder to store the contacts on the external drive>Finish
Browse until you find the file folder to store the contacts on the external drive>Finish
Check your hard drive to ensure the file is there. Open it and see if the addresses did export.
To save contacts as an Outlook .pst file the process is almost identical.
On an external drive (or in the Cloud), create a folder to save your emails and contacts.
Open Outlook>File>Open&Export>Import/Export>Export to a file> Next>Outlook Data File (.pst)>Contacts (scroll until you find your contacts)> browse until you find the file folder to store the contacts on the external drive>Finish
Group Contacts
There may be a more succinct process for backing up groups, but after several attempts, this was the only one that worked for me.
Select a group in your contact list and open it.
Then choose File>SaveAs>Browse to find the file folder where you wish to save the file)>SaveAsType(under File Name)>Select Text Only>Save. Then go to the file, copy the group members (control 'C'). I opted to create a separate sheet in my contacts document (click on the plus sign at the bottom of the spreadsheet to add a sheet). Then type control 'V' to paste the group. You can add as many pages as you need to accommodate your groups.
To back up emails:
Open Outlook>File>Open&Export>Import/Export>Export to a file> Next>Outlook Data File (.pst)>Select the email file you wish to backup>Browse for file storage location and select the folder>I selected Replace duplicates with items exported>Finish
For other email programs, please check with your program’s instructions for backup procedures. Believe me, it is not worth the wasted time or hassle of losing your data.
Hopefully your files are now securely backed up.
The Practical Sort's genius is in organizing, not computer technology. So if you need a hand getting organized, please contact ThePracticalSort.com. Remember part of being organized is having the data you need when you need it. So taking a few minutes of precaution is worth hours of saved time in the long run. Believe me!
Stop, Don't Open That
Last week I was at a meeting where one of my colleagues mentioned that she would share with the group some helpful hints via email. Like clockwork, the next morning there was an email from her with an attachment. She is one of the most process-oriented, organized, and fastidious professionals I have ever met. So it was no surprise that she was prompt with her promise.
Yet, for some reason the hairs on the back of my neck tingled immediately. First clue was that her message was in my Spam folder. Not really a surprise, since messages from those who I rarely receive correspondence occasionally land in Spam.
Secondly, my suspicions were aroused because the email just did not appear legit. Honestly, I cannot articulate what the tell-tale signs were. But I let it sit unopened for a day until I had time to reach out to the sender.
The next day, I sent her an inquiry asking if she had indeed sent us an email with attachment, and to thank her if she did.
Without delay, a group message was sent to my colleagues and I explaining that her account had been hacked, and NOT TO OPEN THE EMAIL.
Thank goodness I responded appropriately to those raised neck hairs. Bottom line: if you have any doubts whatsoever about an email especially if there are any attachments, check with the sender before you open it to verify its veracity. Better safe than infected.
Passwords
Do you find it mind-boggling to keep track of all the passwords but leery of storing them on the cloud? Keep a spreadsheet of passwords that is password protected. Now you only have to recall one password instead of dozens.
Personal Finance Management Software
Personal finance management software such as such as Quicken, Mint, Personal Capital have numerous benefits
Do you still use an old fashioned checkbook and reconciliation process? There are numerous benefits to using personal finance management software such as such as Quicken, Mint, Personal Capital, etc.
1. Save time with easy math calculations, statement reconciliation, and payment tracking.
2. Stay on top of your bills with alerts and payment schedules.
3. Manage your transactions, spending habits, budget, and debt strategies.
4. Track investment performance and net worth.
5. Download the data into your tax preparation software for simplified tax prep.
Click here for PC Magazine's comparison review of the programs they consider to be the "Best Personal Finance Services of 2017." Learn more about the pricing and features of each of their top picks.